5 April, 2022
LawPro, the entity that provides insurance for lawyers, recently advised that they are “seeing a substantial increase in closing proceeds redirection frauds.” This is a phishing scam that can happen to any business, not just lawyers.
Two Toronto men were recently arrested along with 63 others from around the world in an FBI lead investigation into a business email compromise (BEC) scam. The FBI says 2021 losses in the U.S. from BEC were $2.4 billion.
What is a BEC scam?
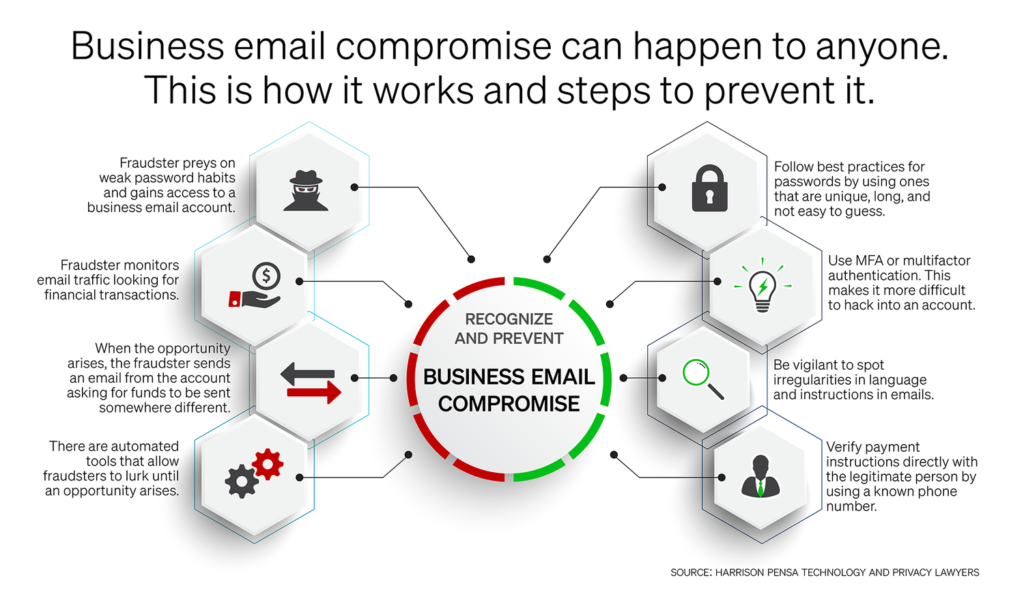
A fraudster gains access to a business email account. That could be an account of a lawyer or other professional, an executive, or someone in an accounting role. The fraudster monitors email traffic in the account looking for financial transactions. When the opportunity arises, they send an email from the account asking for the funds to be sent somewhere different — being an account controlled by the fraudster.
The paying party reacts to what looks like a legitimate request — after all, it’s from a person they are dealing with — and makes the payment to the new account.
How does the fraudster get access to the email account?
A BEC attack happens when the fraudster somehow gets the person’s password. That might be a result of sloppy password habits, such as having an easily guessed or common password. Or the person uses the same password for their work email as other personal accounts, and one of those personal accounts was on a platform that had passwords stolen. Then it’s just a matter of the fraudster matching up the person’s name and trying that password.
This sounds like a lot of work, but there are automated tools available to fraudsters to help them with it.
The victim does not realize their email account has been hacked, because the fraudster just lurks there looking for opportunities. Once they start sending emails to redirect payments, they use tricks such as creating email rules to save email threads to an obscure folder so they can send and receive emails without being noticed.
How can we prevent our email accounts from being hacked?
Adopt best practices for passwords. Most organizations have password polices. Follow them. There is plenty of advice online for effective passwords. For example, make sure they are not short and easily guessed. And don’t use the same password for a work account that you use for anything else.
Use MFA or multifactor authentication. Organizations are increasingly adopting MFA, which makes it much more difficult to hack into an account.
How can we recognize a fraudulent email?
The fraudulent emails can look legitimate. Sometimes they seem odd, because of a reference to an email address that is slightly off, wording that doesn’t seem normal from that person, or an unusual payment method. But not always. The best approach is to treat every email that purports to change payment instructions as a fraud and verify it. Don’t try to verify it by responding to the email, as the fraudster will intercept it, and don’t verify by calling a number in the email. Verify it by calling the apparent sender at a known phone number.
Organizations should have policies in place around when and how to do that.
How can a business reduce its risk?
Businesses should keep up to date with these kinds of frauds and implement internal policies and procedures that adopt best practices. That includes password policies that set out the type of passwords that must be used and can’t be used. And policies that set out when and how to confirm payment instruction changes. Implement MFA wherever possible.
Educate staff through security training about the policies they are to follow, and how to recognize fraud. Maintain awareness with staff by methods such as security campaigns, posters, and notices from third-party victims or advisors.
I’m a victim — now what?
Sometimes financial institutions can reverse fraudulent payments. Contact your financial institution immediately to see if they can do that before the money is gone for good.
If your email account has been compromised, have your IT department or IT service provider freeze the account and change the password. They should investigate the account to look for evidence of what the fraudster did with the account, how long the account was compromised, what the fraudster changed or added to the account, and what emails the fraudster sent. Any such changes need to be reversed.
Notify any other party that might be a potential victim.
The damage may go beyond financial fraud. If someone had access to your email account, they may also have gained access to other systems using a similar login. There is potential for the fraudster to have seen confidential or personal information that is in your emails or other systems. That may lead to the need to notify those parties, and perhaps the privacy commissioner.
David Canton is a business lawyer and trademark agent at Harrison Pensa with a practice focusing on technology, privacy law, technology companies and intellectual property. Connect with David on LinkedIn and Twitter.
Image credit: ©RareStock – stock.adobe.com





